Introduction to Xmas Scan
Nmap Xmas scan was considered a stealthy scan which analyzes responses to Xmas packets to determine the nature of the replying device. Each operating system or network device responds in a different way to Xmas packets revealing local information such as OS (Operating System), port state and more. Currently many firewalls and Intrusion Detection System can detect Xmas packets and it is not the best technique to carry out a stealth scan, yet it is extremely useful to understand how it works.
In the last article on Nmap Stealth Scan was explained how TCP and SYN connections are established (must read if unknown to you) but the packets FIN, PSH and URG are especially relevant for the Xmas because packets without SYN, RST or ACK derivatives in a connection reset (RST) if the port is closed and no response if the port is open. Before the absence of such packets combinations of FIN, PSH and URG are enough to carry out the scan.
FIN, PSH and URG packets:
PSH: TCP buffers allow data transference when you send more than a segment with maximm size. If the buffer isn’t full the flag PSH (PUSH) allows to send it anyway by filling the header or instructing TCP to send packets. Through this flag the application generating traffic informs the data must be sent immediately, the destination is informed data must be sent immediately to the application.
URG: This flag informs specific segments are urgent and must be prioritized, when the flag is enabled the receiver will read a 16 bits segment in the header, this segment indicates the urgent data from the first byte. Currently this flag is almost unused.
FIN: RST packets were explained in the tutorial mentioned above (Nmap Stealth Scan), contrary to RST packets, FIN packets rather than informing on connection termination requests it from the interacting host and waits until getting a confirmation to terminate the connection.
Port states
Open|filtered: Nmap can’t detect if the port is open or filtered, even if the port is open the Xmas scan will report it as open|filtered, it happens when no response is received (even after retransmissions).
Closed: Nmap detects the port is closed, it happens when the response is a TCP RST packet.
Filtered: Nmap detects a firewall filtering the scanned ports, it happens when the response is ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13). Based on the RFC standards Nmap or the Xmas scan is capable to interpret the port state
The Xmas scan, just as the NULL and FIN scan can’t distinguish between a closed and filtered port, as mentioned above, is the packet response is an ICMP error Nmap tags it as filtered, but as explained on Nmap book if the probe is banned without response it seems opened, therefore Nmap shows open ports and certain filtered ports as open|filtered
What defenses can detect an Xmas scan?: Stateless firewalls vs Stateful firewalls:
Stateless or non-stateful firewalls carry out policies according to the traffic source, destination, ports and similar rules ignoring the TCP stack or Protocol datagram. Contrary to Stateless firewalls, Stateful firewalls, it can analyze packets detecting forged packets, MTU (Maximum transmission Unit) manipulation and other techniques provided by Nmap and other scanning software to bypass firewall security. Since the Xmas attack is a manipulation of packets stateful firewalls are likely to detect it while stateless firewalls are not, Intrusion Detection System will also detect this attack if configured properly.
Timing templates:
Paranoid: -T0, extremely slow, useful to bypass IDS (Intrusion Detection Systems)
Sneaky: -T1, very slow, also useful to bypass IDS (Intrusion Detection Systems)
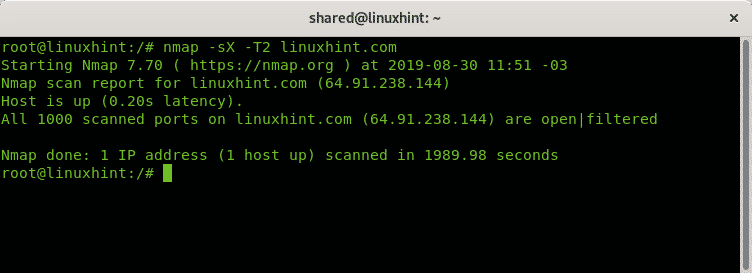
Polite: -T2, neutral.
Normal: -T3, this is the default mode.
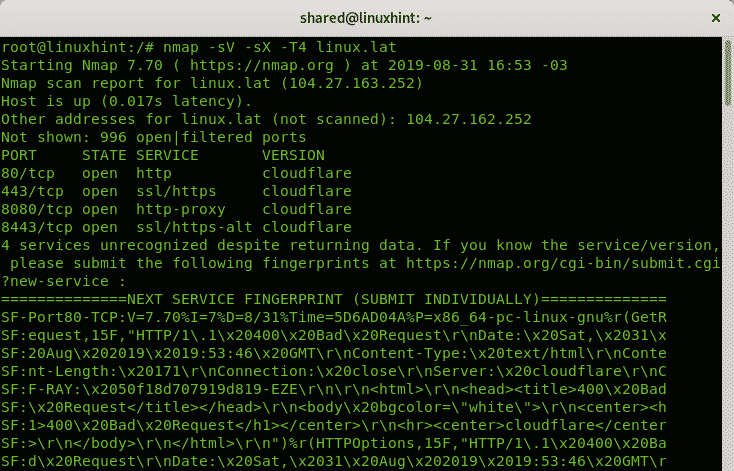
Aggressive: -T4, fast scan.
Insane: -T5, faster than Aggressive scan technique.
Nmap Xmas Scan examples
The following example shows a polite Xmas scan against LinuxHint.
Example of Aggressive Xmas Scan against LinuxHint.com
By applying the flag -sV for version detection you can get more information on specific ports and distinguish between filtered and filtered ports, but while Xmas was considered a stealth scan technique this addition may make the scan more visible to firewalls or IDS.
Iptables rules to block Xmas scan
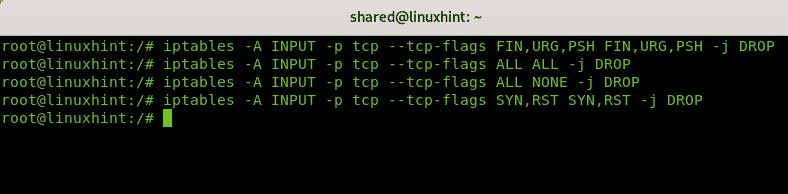
The following iptables rules can protect you from an Xmas scan:
iptables -A INPUT -p tcp --tcp-flags ALL ALL -j DROP
iptables -A INPUT -p tcp --tcp-flags ALL NONE -j DROP
iptables -A INPUT -p tcp --tcp-flags SYN,RST SYN,RST -j DROP
Conclusion
While the Xmas scan isn’t new and most defense systems are capable to detect it becoming an obsolete technique against well protected targets it is a great way of introduction to uncommon TCP segments like PSH and URG and to understand the way in which Nmap analyzes packets get conclusions on targets. More than an attack method this scan is useful to test your firewall or Intrusion Detection System. The iptables rules mentioned above should be enough to stop such attacks from remote hosts. This scan is very similar to NULL and FIN scans both in the way in which they work and low effectivity against protected targets.
I hope you found this article useful as an introduction to Xmas scan using Nmap. Keep following LinuxHint for more tips and updates con Linux,networking and security.
Related articles:
- How to scan for services and vulnerabilities with Nmap
- Using nmap scripts: Nmap banner grab
- nmap network scanning
- nmap ping sweep
- nmap flags and what they do
- OpenVAS Ubuntu Installation and Tutorial
- Installing Nexpose Vulnerability Scanner on Debian/Ubuntu
- Iptables for beginners
Main source: https://nmap.org/book/scan-methods-null-fin-xmas-scan.html