Getting Started with the dd Command
To get started with the dd command, first, open the terminal by pressing Ctrl+Alt+T. Then, run the following command:
Running the above command will display the user manual of the dd command. The dd command is used with some parameters. To list all the available parameters, run the following command in the terminal:
The above command will give you all the options available that can be used with the dd command. This article will not discuss all the options available, but only those related to the given topic. Below are listed some of the most important parameters of the dd command:
- bs=B: This parameter sets the number of bytes B that can be read or written at any time when creating a disk image file. The default value of bs is 512 bytes.
- cbs=B: This parameter sets the number of bytes B that can be converted at a time during any process.
- count=N: This parameter sets the number N of input blocks of data to be copied.
- if=DEST: This parameter takes the file from the destination DEST.
- of=DEST: This parameter saves the file to the destination DEST.
Important Terms to Review
In this tutorial, while discussing the dd command in the forensics context, we will use some technical terms that you must be familiar with before going through the tutorial. The following are the terms which will be used repeatedly throughout the tutorial:
- MD5 checksum: The MD5 checksum is the 32-character string generated by a hashing algorithm that is unique for different data. No two different files can have the same MD5 checksum.
- md5sum: The md5sum is a command-line utility used to implement a 128-bit hashing algorithm and is also used to generate an MD5 checksum of unique data. We will use md5sum in the tutorial in this article to generate MD5 checksums of data.
- Disk Image File: The disk image file is the exact copy of the disk from which it is created. We can say that it is a point in time snapshot of the disk. We can restore our disk data from this disk image file when needed. This file is exactly the same size as the disk itself. We will use the dd command to create a disk image file from the disk.
Tutorial Overview
In this tutorial, we will create a backup system and verify whether the data is backed up accurately with the dd and md5sum commands. First, we will specify the disk of which we want to create a backup. Next, we will use the dd command-line utility to create a disk image file of the disk. Then, we will create MD5 checksums of both the disk and disk image file to verify whether the disk image file is accurate. After this, we will restore the disk from the disk image file. We will then generate an MD5 checksum of the restored disk and verify it by comparing it with the MD5 checksum of the original disk. Finally, we will change the disk image file and create the MD5 checksum from this changed disk image file to test the accuracy. The MD5 checksum of the changed disk image file should not be the same as that of the original file.
The dd Command in a Forensics Context
The dd command comes by default with many Linux distributions (Fedora, Ubuntu, etc.). Besides performing simple actions on data, the dd command can also be used to perform some basic forensics tasks. In this tutorial, we will use the dd command, along with md5sum, to verify accurate disk image creation from the original disk.
Steps to Follow
Below are the steps required to verify a sound disk image using the md5sum and dd commands.
- Create MD5 checksum of the disk using the md5sum command
- Create image file of the disk using the dd command
- Create MD5 checksum of the image file using the md5sum command
- Compare the MD5 checksum of the disk image file with the MD5 checksum of the disk
- Restore the disk from the disk image file
- Create MD5 checksum of the restored disk
- Test MD5 checksum against the altered image file
- Compare all the MD5 checksums
Now, we will discuss all the steps in detail, to better show how things work with these commands.
Creating an MD5 checksum of the Disk
To get started, first log in as a root user. To log in as a root user, run the following command in the terminal. You will then be prompted for the password. Enter your root password and get started as a root user.
Before creating the MD5 checksum, first, select the disk you want to use. To list all the available disks on your device, run the following command in the terminal:
For this tutorial, I will use the /dev/sdb1 disk available on my device. You can choose an appropriate disk from your device to use.
NOTE: Choose this disk wisely and use the dd command-line utility in a safe environment, as it can have devastating effects on your disk if not used properly.
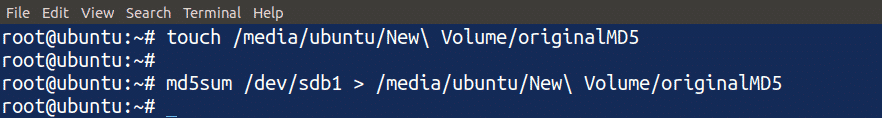
Create an original MD5 file in the /media file and run the md5sum command in the terminal to create an MD5 checksum of the disk.
ubuntu@ubuntu:~$ md5sum /dev/sdb1 > /media/originalMD5
When you run the above commands, it creates a file in the destination specified by the parameter and saves the MD5 checksum of the disk (/dev/sdb1, in this case) in the file.
NOTE: The md5sum command can take some time to run, depending on the size of the disk and the speed of your system’s processor.
You can read the MD5 checksum of the disk by running the following command in the terminal, which will give the checksum, as well as the disk name:
Creating an Image File of the Disk
Now, we will use the dd command to create an image file of the disk. Run the following command in the terminal to create an image file.
This will create a file in the specified location. The dd command does not work alone. You must also specify some options within this command. The options included with the dd command have the following meaning:
- If: The path to input the image of the file or drive to be copied.
- of: The path to output the image file obtained from the if
- bs: The block size; in this example, we are using a block size of 1k or 1024B.
NOTE: Do not try to read or open the disk image file, as it is the same size as that of your disk, and you may end up with a handed system. Also, be sure to specify the location of this file wisely due to its larger size.
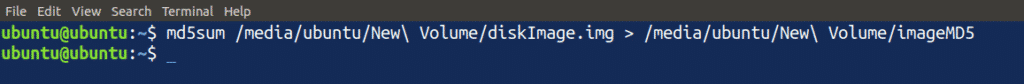
Creating an MD5 checksum of the Image File
We will create an MD5 checksum of the disk image file created in the previous step using the same procedure performed in the first step. Run the following command in the terminal to create an MD5 checksum of the disk image file:
This will create an MD5 checksum of the disk image file. Now, we have the following files available:
- MD5 checksum of the disk
- Disk image file of the disk
- MD5 checksum of the image file
Comparing MD5 Checksums
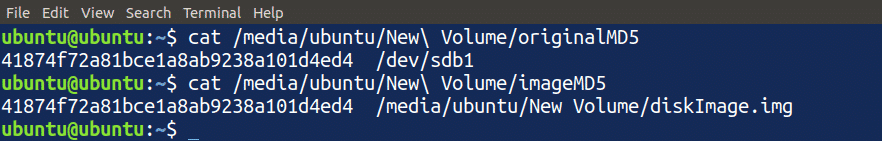
So far, we have created an MD5 checksum of the disk and of the disk image file. Next, to check whether an accurate disk image has been created, we will compare the checksums of both the disk itself and the disk image file. Enter the following commands in your terminal to print the text of both files to compare the two files:
ubuntu@ubuntu:~$ cat /media/imageMD5
These commands will display the content of both files. The MD5 checksum of both files must be the same. If the MD5 checksums of the files are not the same, there a problem must have occurred while creating the disk image file.
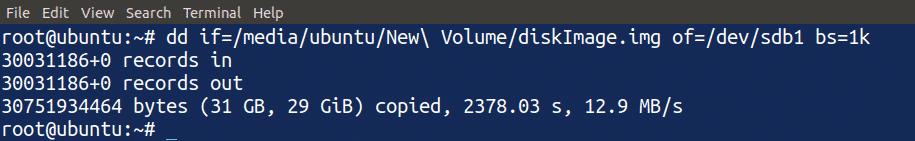
Restoring the Disk from the Image File
Next, we will restore the original disk from the disk image file using the dd command. Type the following command in the terminal to restore the original disk from the disk image file:
The above command is similar to the one used to create a disk image file of the disk. In this case, however, the input and output are switched, reversing the flow of data to restore the disk from the disk image file. After entering the above command, we have now restored our disk from the disk image file.
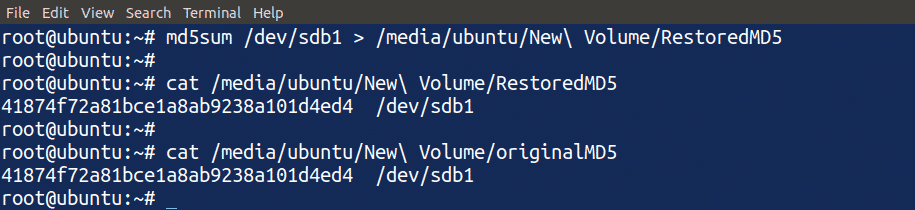
Creating an MD5 Checksum of the Restored Disk
Next, we will create an MD5 checksum of the disk restored from the disk image file. Type the following command to create an MD5 checksum of the restored disk:
Using the above command, created an MD5 checksum of the restored disk and displayed it in the terminal. We can compare the MD5 checksum of the restored disk with the MD5 checksum of the original disk. If both are the same, this means that we have accurately restored our disk from the disk image.
Testing the MD5 Checksum Against the Altered Image File
So far, we have compared the MD5 checksums of accurately created disks and disk image files. Next, we will use this forensics analysis to check the accuracy of an altered disk image file. Change the disk image file by running the following command in the terminal.
Now, we have changed our disk image file, and it is no longer the same as before. Note that I have used the “>>” sign instead of “>.” This means I have appended the disk image file, instead of rewriting it. Next, we will create another MD5 checksum of the changed disk image file using the md5sum command in the terminal.
Entering this command will create an MD5 checksum of the changed disk image file. Now, we have the following files:
- Original MD5 checksum
- Disk Image MD5 checksum
- Restored disk MD5 checksum
- Changed disk image MD5 checksum
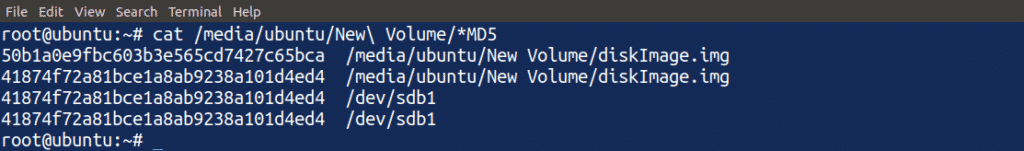
Comparing all the MD5 Checksums
We will conclude our discussion by comparing all the MD5 checksums created during this tutorial. Use the cat command to read all the MD5 checksum files to compare them with one another:
The above command will display the content of all the MD5 checksum files. We can see from the image above that all the MD5 checksums are equal, except for the top one, which was created with the changed disk image file. So, in this way, we can verify the accuracy of the files using the dd and md5sum commands.
Conclusion
Creating a backup of your data is an important strategy to restore it in case of disaster, but the backup is useless if your data gets corrupted in the middle of transfer. To ensure that the data transfer is accurate, you can use some tools to perform actions on the data to authenticate whether the data has been corrupted through the copying process.
The dd command is a built-in command-line utility used for creating image files of the data stored in disks. You can also use the md5sum command to create an MD5 checksum of the newly created image, which authenticates the accuracy of the copied data, to perform forensics on the transferred data along with the dd command. This tutorial discussed how to use the dd and md5sum tools in a forensics context to ensure the accuracy of copied disk data.